The Department of Homeland Security (DHS) reminds us that a non-profit’s office security plan “should take an ‘all hazards’ approach… The probability that a specific hazard will impact your business is hard to determine. That’s why it’s important to consider many different threats and hazards and the likelihood they will occur.”
DHS’s collection of business preparedness resources helps all types of organizations (including non-profits) structure their all-hazards risk assessment and planning. For example, worksheets like this one can help focus the conversation, especially when you have diverse stakeholders within a large organization (as can often be the case in non-profits).
The Four-Step All-Hazards Security Planning Process
Many security experts advise the following four-step all-hazards security planning process, based on DHS recommendations:
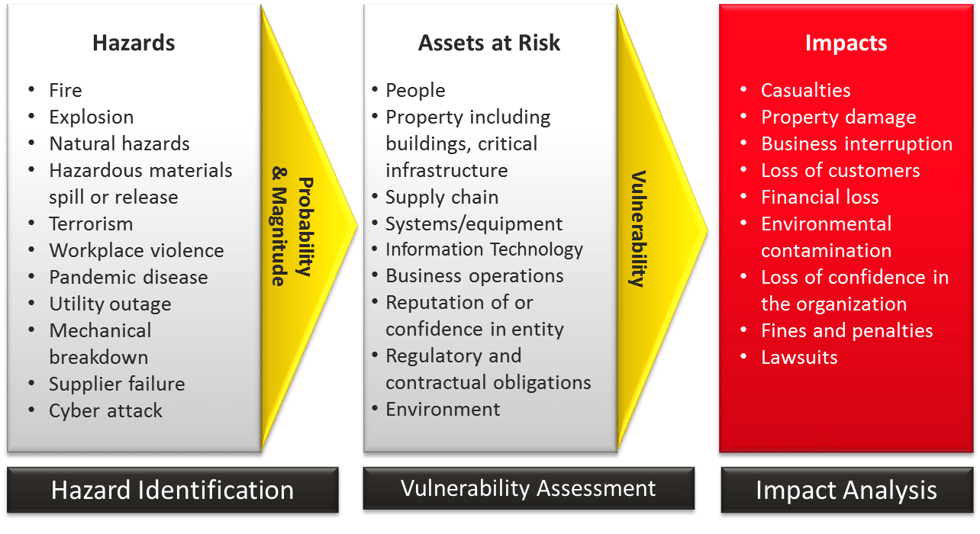
All-hazard office security plan considerations (source: DHS)
Step 1: Identify Hazards
Take a comprehensive look at the many hazards your organization might face; this recently updated list on the Ready.gov website is an excellent starting place.
It’s easy to become too focused on new headlines. That’s never been more relevant than at the time of this writing, with ongoing civil unrest and protests, a global pandemic, wildfires, and tropical-storm/hurricane-related flooding. These enormous threats can easily pull focus from the more immediate risks that could post an even bigger threat. For example, seemingly mundane risks like fire hazards caused by aging wiring can be so familiar we often forget how deadly they can be.
As you go through the checklist of potential hazards, rate each hazard in terms of probability (how likely it is to happen) and magnitude (how badly will it disrupt your operations).
For example, you might rate a fire as a high probability event that’s fairly low magnitude. (There are an estimated 50,000 nonresidential building fires each year, but those 50,000 fires are often confined to a single room, and result in fewer than 1,000 injuries, less than 0.09% of which prove fatal.)
Conversely, a targeted active shooter event at your office is an extremely low probability (a few dozen occur each year). But it’s certainly high magnitude: each year, dozens of people are injured or killed, and entire communities are psychologically impacted. Many non-profits are not able to recover from the financial liability and reputational damage created by a workplace attack.
See our most Frequently Asked Questions about applying for a non-profit security grant
Step 2: Consider Your Assets and their Vulnerabilities
When considering assets, DHS specifies that, “injuries to people should be the first consideration of the risk assessment. Hazard scenarios that could cause significant injuries should be highlighted to ensure appropriate emergency plans are in place.”
Bearing that in mind, and understanding that people are no doubt your most valuable assets, they are far from your only assets. Your asset list will include both physical assets (buildings, equipment, etc.), as well as less tangible assets (data, reputation, community confidence, worker/volunteer/client peace-of-mind, etc). Rate these in terms of how vital they are to your organization and its functioning or survival.
Now identify each asset’s vulnerabilities:
- What makes that asset likely to fall prey to one of the hazards you listed in Step 1?
- Is there a point of failure that exposes that asset?
- Is the asset especially attractive for some reason?
In general, a vulnerability will:
- Increase the probability of an event (it makes the event more likely)
- Increases the event’s magnitude (making it more damaging), or
- Increase both the probability and the magnitude
Step 3: Assess the Impacts
Go through your list of hazards (from Step 1). Consider the potential impact each hazard has on each asset (identified in Step 2).
For example, if you operate a food pantry and health clinic, your assets may include:
- workers/volunteers
- your building
- donated food and medical supplies
- vehicles
- office equipment
- decades of paper files
- your reputation
A severe flood may destroy badly needed supplies and sweep away decades of records, but it’s unlikely to harm your workers/volunteers, clients, or reputation. Meanwhile, ongoing protests near your poorly secured building may mean that the doctors and workers who provide services to your clients are no longer willing (or able) to volunteer. Similarly, a board member behaving inappropriately or misappropriating funds may cause no material damage to any asset, and still cripple an organization because of the reputational damage or financial fallout from litigation.
Step 4: Weigh Possible Mitigations
Mitigation reduces the impact a hazard can have on your assets (and thus your non-profit). Mitigation might do this at any stage—by eliminating a hazard or vulnerability, by reducing the probability of an event, by lessening the magnitude of the event, or by easing its impact. Some mitigation strategies reduce risks at multiple stages. For example, installing a new fire suppression system won’t just reduce the probability and magnitude of a fire (addressing the hazard directly); it also reduces your insurance rate, allowing you to purchase more coverage (and thus ease the impact if a freak accident should occur). Likewise, installing a bullet-resistant or VirusGuard™ barrier reduces specific threats (like infectious disease or armed attack), decreases associated risks (deters verbal conflict), and increases the sense of safety and security among staff and volunteers.
Embracing the All-Hazards Process
Total Security Solutions CEO Jim Richards applauds any planning process that gets people thinking comprehensively about security.
“As the name implies, we develop total security solutions; they are attractive, integrated solutions that increase safety and security in general. We can offer the physical means to protect from a range of threats—both violent and disease. But comprehensive security always has to come back to a human-centered solution. We’re more than happy to help people think through all the hazards—including ones building occupants might accidentally introduce, just going about their daily business. We like helping organizations formulate a solution that addresses many risks, while making it easier and safer for them to fulfill these important missions on a daily basis.”